In today’s digital age, Cybersecurity Essentials: The Best Software to Protect Your Data has become a crucial aspect of personal and professional life. With the increasing amount of sensitive information being stored and transmitted online, it is essential to have the right tools and software in place to safeguard against cyber threats. Cybersecurity software offers protection against malware, phishing attacks, and unauthorized access, ensuring the integrity and confidentiality of your data.
When it comes to Cybersecurity Essentials: The Best Software to Protect Your Data, individuals and businesses often look for reliable antivirus programs, firewalls, and encryption tools to enhance their digital security. These tools are designed to detect and eliminate various types of cyber threats, such as viruses, ransomware, and spyware, while also providing a secure barrier against unauthorized access to networks and sensitive information. Additionally, cybersecurity software can offer features such as real-time threat detection, secure password management, and regular software updates to stay ahead of emerging threats. By investing in the right cybersecurity essentials, users can mitigate the risks associated with cyber attacks and minimize the potential impact on their data and privacy.
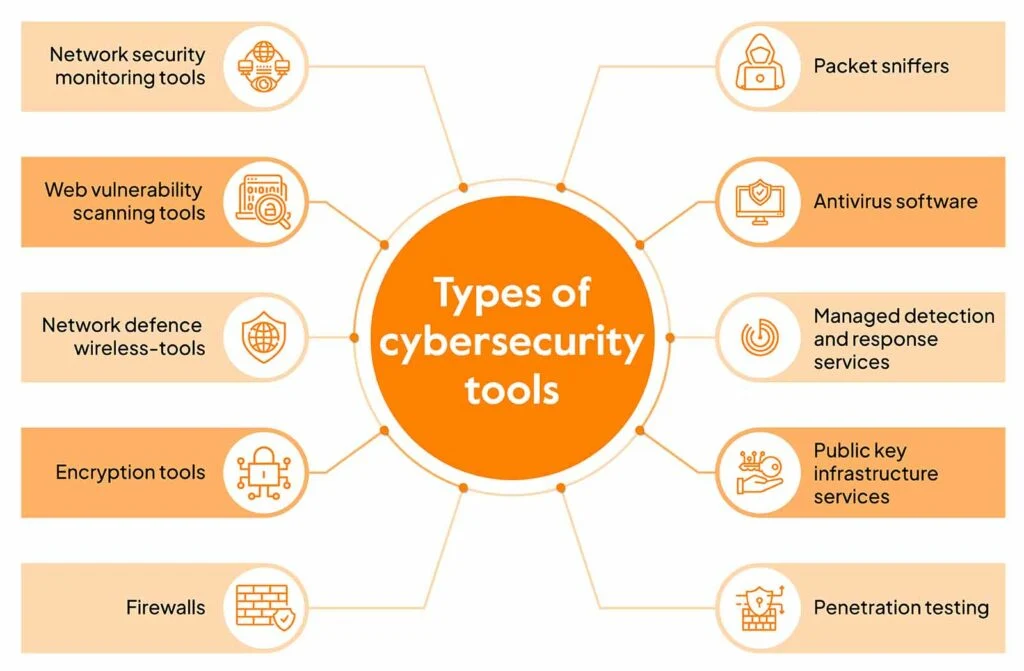
The Importance of Cybersecurity Software
Cybersecurity software is essential for protecting your data and digital assets from cyber threats such as malware, ransomware, and phishing attacks. These software solutions are designed to detect, prevent, and respond to cyber threats, helping to keep your personal and business information safe and secure. With the increasing frequency and sophistication of cyber attacks, investing in reliable cybersecurity software is crucial for safeguarding your digital presence.
By using cybersecurity software, you can establish a strong defense system that monitors and blocks potential security breaches, ensuring that your sensitive data remains protected. Additionally, these software solutions often include features such as firewall protection, antivirus scanning, and real-time threat intelligence to proactively defend against emerging cyber threats.
Antivirus Software for Comprehensive Protection
Antivirus software is a fundamental component of cybersecurity, as it is designed to detect and remove malicious software from your devices. These programs continuously scan your system for known malware signatures and suspicious behavior, providing a crucial layer of defense against viruses, Trojans, and other forms of malware. By regularly updating your antivirus software, you can ensure that your devices are equipped to combat the latest cyber threats.
Furthermore, modern antivirus software often includes features such as web protection, email scanning, and file quarantine to safeguard your online activities and prevent malware from infiltrating your system through various channels.
Firewall Protection for Network Security
A firewall is a vital cybersecurity tool that acts as a barrier between your internal network and external threats. It monitors and controls incoming and outgoing network traffic based on predetermined security rules, effectively preventing unauthorized access and potential cyber attacks. By implementing a robust firewall solution, you can fortify your network security and minimize the risk of data breaches and intrusions.
Firewall protection can be deployed at both the network level and individual device level, offering a versatile defense mechanism for safeguarding your digital infrastructure. Additionally, modern firewalls often incorporate advanced features such as intrusion detection and prevention, deep packet inspection, and application-layer filtering to enhance security capabilities.
Encryption Software for Data Privacy
Encryption software is essential for protecting the confidentiality and integrity of your sensitive data. By using encryption algorithms, this software converts your data into an unreadable format that can only be deciphered with the appropriate decryption key. This ensures that even if your data is intercepted or compromised, it remains incomprehensible to unauthorized parties.
Whether you are transmitting data over the internet, storing information on your devices, or sharing files with others, encryption software plays a critical role in maintaining data privacy. It enables you to secure your communications, safeguard your intellectual property, and comply with data protection regulations by rendering your sensitive information inaccessible to unauthorized entities.
Phishing Protection Software for Email Security
Phishing protection software is designed to detect and block phishing attempts, which are fraudulent efforts to obtain sensitive information such as login credentials and financial details. This type of cybersecurity software analyzes incoming emails and identifies potential phishing threats, helping users avoid falling victim to deceptive schemes and social engineering tactics.
By leveraging advanced detection algorithms and threat intelligence, phishing protection software enhances email security by alerting users to suspicious links, attachments, and requests for personal information. It provides an additional layer of defense against phishing attacks, empowering individuals and organizations to mitigate the risks associated with malicious email content.
Endpoint Security Software for Device Protection
Endpoint security software is designed to secure individual devices such as computers, laptops, and mobile devices from cyber threats. It encompasses a range of security measures, including antivirus protection, firewall management, and device encryption, to defend against malware and unauthorized access. By implementing endpoint security solutions, organizations can protect their endpoints and prevent potential security breaches.
Moreover, endpoint security software often includes features such as device management, application control, and remote monitoring to ensure that devices are compliant with security policies and free from vulnerabilities. This comprehensive approach to device protection helps to mitigate the risks associated with endpoint security and maintain a secure digital environment.
Security Information and Event Management (SIEM) Software for Threat Detection
SIEM software is a powerful tool for monitoring and analyzing security events within an organization’s IT infrastructure. By collecting and correlating data from various sources, including network devices, servers, and applications, SIEM solutions enable proactive threat detection and rapid incident response. This real-time visibility into security events allows organizations to identify and mitigate potential cyber threats effectively.
Furthermore, SIEM software offers features such as log management, security analytics, and compliance reporting, enabling organizations to gain valuable insights into their security posture and regulatory adherence. By leveraging SIEM technology, businesses can strengthen their overall cybersecurity strategy and defend against advanced threats through continuous monitoring and analysis.
Backup and Recovery Software for Data Resilience
Backup and recovery software is essential for ensuring the resilience of your data in the face of cyber incidents, system failures, and human errors. By regularly backing up your critical data and applications, you can mitigate the impact of data loss and downtime, enabling swift recovery in the event of unforeseen disruptions. This proactive approach to data protection is crucial for maintaining business continuity and minimizing the potential consequences of data-related incidents.
Moreover, modern backup and recovery solutions offer features such as automated backups, data deduplication, and cloud integration, providing scalable and secure options for safeguarding your data. By implementing a robust backup and recovery strategy, you can fortify your data resilience and minimize the risks associated with data loss and operational disruptions.
| Software | Features |
|---|---|
| Firewall | Monitors and controls incoming and outgoing network traffic |
| Antivirus | Detects and removes malware, viruses, and other malicious software |
| Virtual Private Network (VPN) | Encrypts internet traffic and hides IP address to ensure secure browsing |
| Endpoint Protection | Secures individual devices from cyber threats |
| Multi-factor Authentication | Requires multiple forms of verification to access accounts |
Cybersecurity essentials are crucial for protecting your data from cyber threats. Using software such as firewall, antivirus, VPN, endpoint protection, and multi-factor authentication can help safeguard your information and maintain a secure digital environment.